In a trivial file sharing scheme, there are users and a server that accepts a file from one user and allows others to download it. There are two weak points in this scenario: the network bandwidth of the distribution server and the centralization factor. The server’s network channel can provide good download speeds to several users, for example, a hundred, but if you imagine that thousands of users are downloading from the server at the same time, alas, the download speed for everyone will become depressing. You can also mention the speed of the server’s hard drives, which in some cases contributes to a drop in download speed no worse than a weak network channel. All this is the consequence of a centralized architecture, the main danger of which lies in the fact that a server leaving the network is tantamount to a complete loss of the ability to download the file it stores..
BitTorrent is the most common protocol for exchanging files peer-to-peer, that is, directly between users without dependence on the central server. 
BitTorrent
BitTorrent supports several operating modes, which in most cases are combined together: work via tracker, PEX (Peer EXchange) and DHT (Distributed Hash Table). First things first.
First, you need to clarify the basic terminology related to torrent distribution participants:
Peer – a general designation for a participant in the process;
Seed, seed - a peer that has the entire file. The user who creates the distribution is clearly called a seeder, since at the initial stage only he has the entire file. This is why there is usually only one seeder in a new distribution. If you downloaded the entire file and did not leave the distribution, then you also become a seeder;
Leecher - a peer that downloads a file, but has not yet downloaded it completely. He can also distribute fragments that he has already downloaded to other peers;
SuperSeed is a seed in a special distribution mode, when it gives each downloader only unique fragments of files, thereby forcing other participants to be more active (exchange missing parts among themselves).
Tracker is a server that distribution participants access to publish information about themselves and receive information about other exchange participants. A user who has not yet downloaded the file, after receiving a list of peers, knocks on their door with a request to give out part of the file. To implement the possibility of fragmented file downloading (rather than sequential from the first to the last byte in a row), the torrent distribution contains hashes of fragments of the final file. This allows you to download a file in separate parts from different users and check their integrity. The mission of the tracker is to accumulate information about the distribution participants and provide this information to the participants themselves. The torrent tracker does not in any way touch the final file, the exchange of which it provides; it only brings together the distributors and downloaders.
To minimize the consequences of a torrent tracker failure, you can specify several trackers when creating a distribution. In addition, anyone can display the distribution on the new tracker. Thus, interruptions with one of the servers do not deprive the ability to download and distribute.
PEX (Peer EXchange) — extension of the BitTorrent protocol for exchanging lists of participants. The implementation is simple: in addition to file fragments, users exchange additional messages that contain lists of participants who have connected and disconnected from the distribution. This helps new users quickly integrate into the process of downloading a file, since they do not need to wait for the distribution node to contact the tracker, where it will receive a list of newcomers. Also, for the downloading participant, a new source of peers appears in addition to the torrent tracker.
Although simple in design, some BitTorrent clients have their own implementation of PEX that is not compatible with others. In addition, PEX is not a panacea, since it can only help those users who are already connected to the distribution (because PEX messages go through the usual BitTorrent protocol in the form of additional packets).
DHT (Distributed Hash Table) — a protocol that allows BitTorrent clients to find each other without using a tracker. DHT is fundamentally similar to PEX with the main difference being that it operates separately from the main BitTorrent protocol.
Each connected BitTorrent client is a separate node in the DHT network. It has its own unique ID, randomly selected from the same 160-bit space as torrent infohashes. Each node maintains a routing table containing contact information for many nodes "closer" to it, and for several more distant ones. The "closeness" of two nodes is calculated from the "similarity" of their IDs, and has nothing to do with their geographic proximity.
When a node wants to find peers for a particular distribution, it compares the infohash of that distribution with the IDs of the nodes it knows, and then sends a request to the node whose ID is most similar to this infohash. The next node, in turn, returns the address of the node whose ID is even closer to the torrent's infohash. Thus, requests from clients participating in the distribution of a torrent with a certain infohash gradually flow to the nodes whose IDs are most similar to the infohash of the distribution. These nodes remember previous requests from participants for a specific torrent and all subsequent nodes that request will return the addresses of previous peers from the same distribution.
The DHT database is stored by the torrent client regardless of active distributions and is maintained until shutdown or restart, regularly accepting requests from other participants and checking nodes from its list for activity. The DHT database is replenished at any opportunity: when receiving a list of participants from torrent trackers, or from other peers via PEX or DHT.
DHT provides an alternative way to publish a torrent without specifying a tracker. As a rule, such distributions are distributed as a text link instead of a torrent file. The line is called a magnet link and necessarily contains the infohash of the distribution, which allows you to find participants in the distribution via DHT. However, the magnet link may contain the address of the torrent tracker, which in most cases speeds up the search for peers. It should be noted that a magnet link and a torrent file without specifying a tracker are useless if the end user does not have active DHT connections through which he can find a peer participating in the distribution with the desired infohash.
A lot of explanatory material has been created about the basic principles of BitTorrent, so, having understood the essence, let’s move on to the main topic of the article.
BitTorrent to I2P
The idea of file sharing through hidden networks like I2P is not new. For the average user, I2P torrent is notable for the practical impossibility of blocking distributions and trackers on the part of providers, since I2P is a hidden network where the goal of everything is anonymity and the inability to track the source of traffic. The general paradigm of BitTorrent, like any peer-to-peer exchange, implies a direct connection between users. It is this feature that makes conventional torrents unsuitable for distributing files, the distributors of which Big Brother wants to catch and punish. For example, in some European countries much attention is paid to the fight against domestic piracy: games, films, TV series. Law enforcement officers, having connected to the distribution, track by IP address who is participating in the distribution of the cracked game, and then the user receives either a chain letter or a police squad, depending on the level of copying hysteria in the region.
It is considered unethical to publicly discuss the topic of anonymous file sharing, since our average person knows a circle of people who dream of anonymity: pedophiles, drug addicts, extremists, sectarians, sectarian drug addicts, and so on; watch the latest list on federal television channels. However, to a free-thinking and healthy person, the scope of application of anonymous torrents is easy and without remorse. Remember WikiLeaks and other revelations of inhumanity, which for a healthy person are a crime, but according to sometimes absurd laws, the dissemination of information about such crimes is already a crime like disclosing state secrets. The possibility of secretly transferring files in such cases is equal to preserving one’s own life, health and freedom. The need for anonymity is a broad topic, in which there is a place for a corrupt official, a mediocre anime fan, whistleblowers of lawlessness, and - they tell the truth on TV! - criminals. As for criminals: they do not need this article; they have already been successfully using technologies for a long time, which, in principle, cannot be effectively blocked, and therefore prohibited. This material is addressed to a wide audience and is educational in nature, so that free technologies belong to the people, and not to a narrow group of people.
Resistance to censorship on the side of Internet providers and anonymity to distribution participants is entirely ensured by I2P technology. When observing from the outside, it is almost impossible to track the movement of I2P traffic and, therefore, its source. All users and servers have cryptographic IDs instead of IP addresses. Identifiers have nothing to do with the actual location of a network participant, but allow you to contact him. Read more about I2P in separate article, which answers most questions (and also look at other articles on the topic in my profile).
There are several BitTorrent clients that can work via I2P. New solutions appear periodically or old ones are no longer supported by developers. Be that as it may, all applications in this category are divided into two types: those that can work both via the regular Internet and via I2P, and those that are created exclusively to work via a hidden network.
Using a multi-network torrent client can be dangerous if used improperly, as the IP address can be leaked. For example, a user started downloading something via I2P, but he has active DHT connections from the regular Internet, and his client periodically accesses torrent trackers located outside hidden networks. If a request comes from a non-anonymous network that contains the infohash of a dubious I2P seed, the torrent application will respond positively and begin relaying the seed from the darknet somewhere out there, perhaps to Big Brother. The ensuing consequences of leaking an IP address in a dubious distribution are difficult to predict, but nothing pleasant will probably come of it.
On the other hand, multi-network torrent clients can be very useful for deliberate cross-network torrenting. For example, having downloaded a movie from a clearnet tracker (from a torrent tracker from the regular Internet), it can be distributed via I2P for those who for some reason cannot or do not want to use a traditional torrent. In this case, it is important not to change the distribution so that its infohash is identical to the original one. This will provide the maximum number of peers across all possible channels for new users: for those who download only via I2P, and those who combine sources from different networks.
The average I2P network speed at the time of writing is 40Kb/sec. There are jumps over 100Kb/sec, a matter of chance, but in general, with a standard tunnel length (incoming and outgoing tunnels by default have a length of three transit nodes), the speed fluctuates in the range of 20-50Kb/sec. It turns out that the real throughput of the seed is not decisive; it delivers the file to a specific user at a speed of up to 100Kb/sec. This is the speed of a specific peer-to-peer connection, which depends on a lot of factors inherent in I2P, for example, the quality of transit nodes and their number between users. The speed will be determined by the worst member of the chain.
Leechers in an I2P torrent distribution play a significant role in accelerating the entire swarm (the totality of all participants in the distribution is called a swarm). Despite the low average speed for one connection, when downloading and distributing popular torrents in I2P, the speed reaches 2Mb/sec. This is possible thanks to the collectivity factor: participants distribute downloaded fragments to each other, forming new peer-to-peer connections among themselves. Many slow connections provide a good final speed, just as streams gather to form full-flowing rivers. In fact, the BitTorrent protocol was created specifically to distribute the load of file sharing, and its architecture fits perfectly with I2P.
Torrent client I2PSnark
A list of existing torrent clients that support work via I2P can be seen in i2pd documentation. If you think the list is incomplete, you can add. Within the framework of this material, only I2PSnark will be covered, since it has been the best solution for I2P torrents for many years. In addition to decent functionality, it is an I2P-only client, that is, it can work exclusively via the I2P network, which relieves inexperienced users from the threat of IP address leakage.
I2PSnark appeared almost simultaneously with the I2P network itself (~2003). To this day he is part Java router I2P, which includes a number of applications in addition to the main function of connecting the user to a hidden network. I2PSnark interacts with an I2P router using the I2CP protocol, which is supported in an alternative, lighter and faster router i2pd, executed in C++. To use I2PSnark separately from a Java router, you must use I2PSnark standalone. You can build the binary file yourself from the source code, or use the assembly from the project I2P+, which is a soft fork of the main I2P router with minor changes. The direct link to download the I2PSnark standalone binary is provided on the one mentioned above documentation page i2pd.
Java applications require a special execution environment on your device (Java Virtual Machine) to run. You can install Java on almost any modern operating system. Download the latest release for Linux, Mac or Windows at official page.
Before using I2PSnark standalone, you need to enable the I2CP interface, which is disabled by default in i2pd. This is done through the configuration file i2pd.conf: uncomment the line enabled = true In section [i2cp] and restart i2pd. 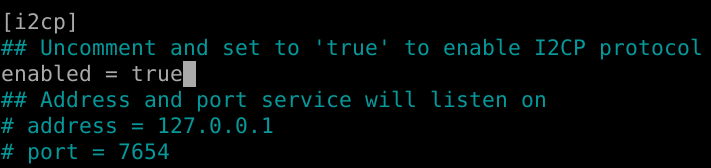
You can find out where to find the configuration file on your system on the main page of the i2pd web interface, which by default is available at http://127.0.0.1:7070. Look at the line Data path.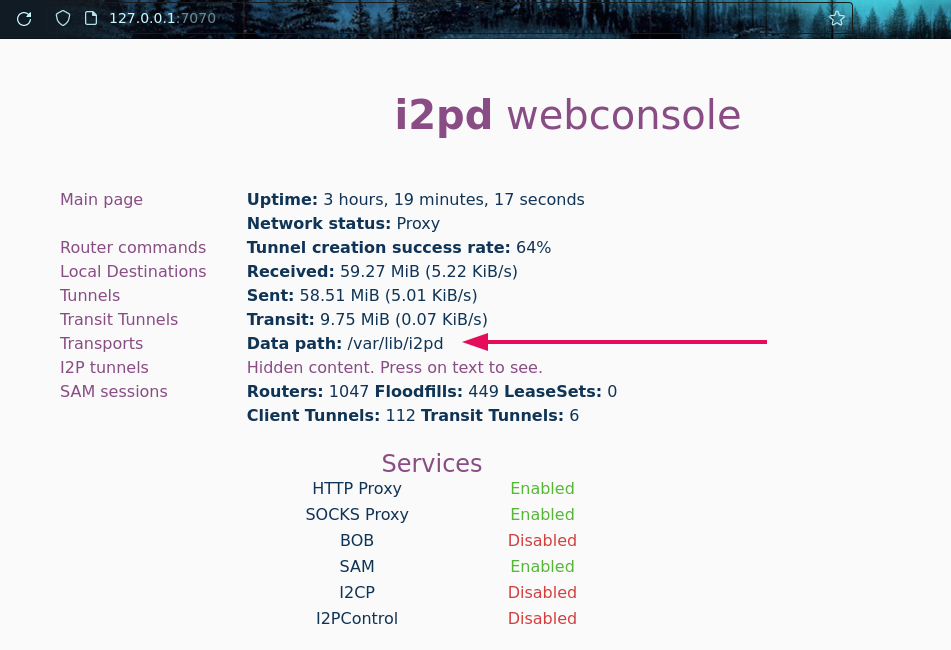
The downloaded I2PSnark standalone archive contains files launch-i2psnark And launch-i2psnark.bat. Use a bat file to run on Windows and a file without an extension in the name in any other case. When used on unix-like operating systems, do not forget to make the file executable before running (chmod +x launch-i2psnark).
You need to interact with the running I2PSnark through the web interface, available by default at http://127.0.0.1:8002. It is intuitive and easy to learn. To change the language to Russian, go to the settings (lowest button, icon with a gear), in the "User interface" section, change "Language" and click on the "Save Configuration" button below.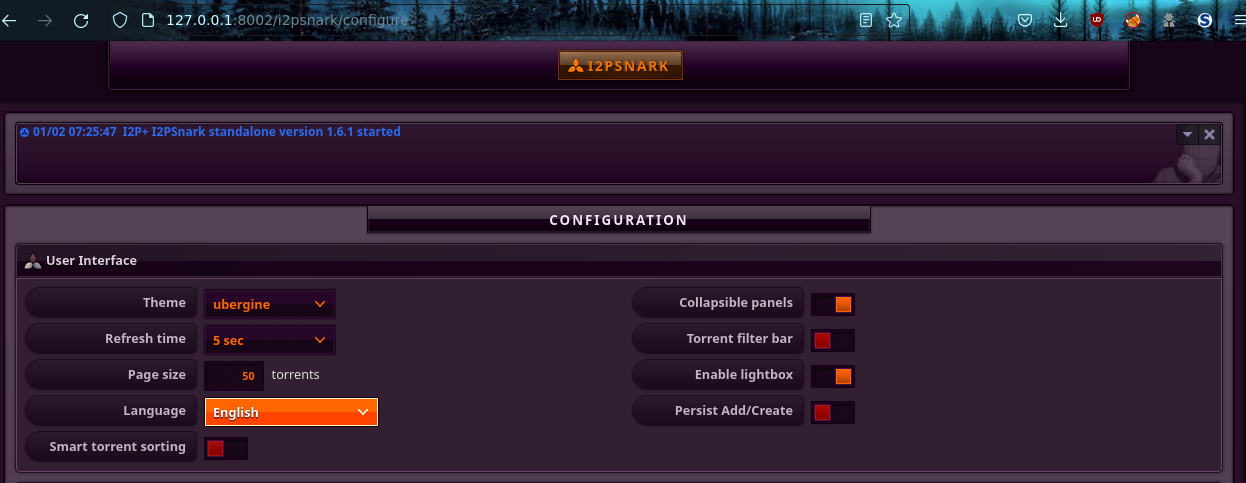
Pay attention to the "Tunnel Configuration" section, which is responsible for incoming and outgoing tunnels. 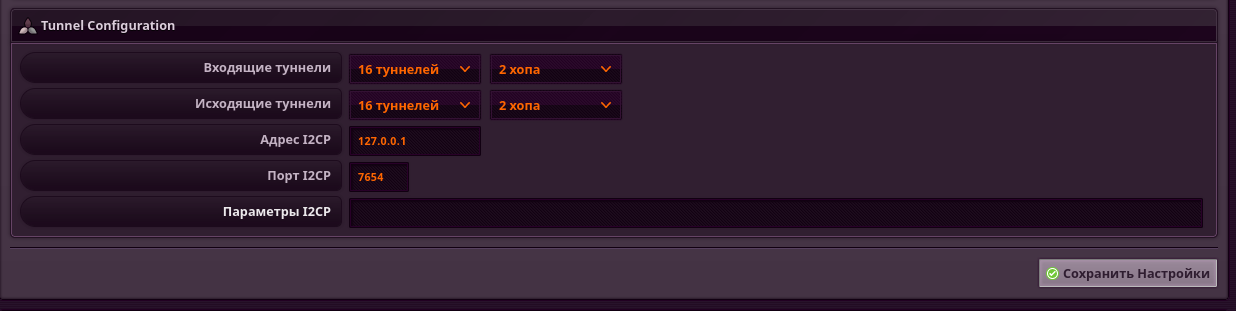
Hops are the length of tunnels at transit nodes. The longer the length, the more anonymous and slower the tunnels. By default, three-hop tunnels are used, but for domestic use it is quite normal to install two or even one hop.
It is possible to run multiple instances of I2PSnark on one device: short tunnels for uploading and downloading regular content, and long tunnels for working with more sensitive material. To do this, copy the entire I2PSnark folder and change the file in the copied directory jetty-i2psnark.xml: find the value "port" and change the port number on which the web interface will be available. 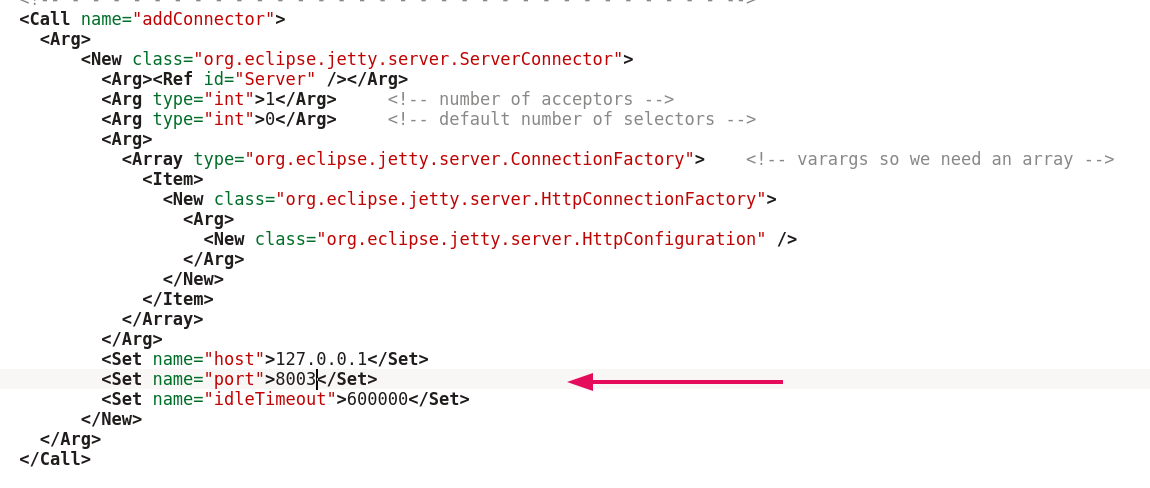
For example, one instance of I2PSnark could use the port 8002, and second 8003. To make it more difficult to confuse which instance you have open in your browser (with long or short tunnels), use different themes.
Note: every time I2PSnark is launched, it changes its I2P identifier, which is visible to other file sharing participants..
Uploading files and creating your own distribution
To join the distribution, open the add menu (top button with the plus icon). 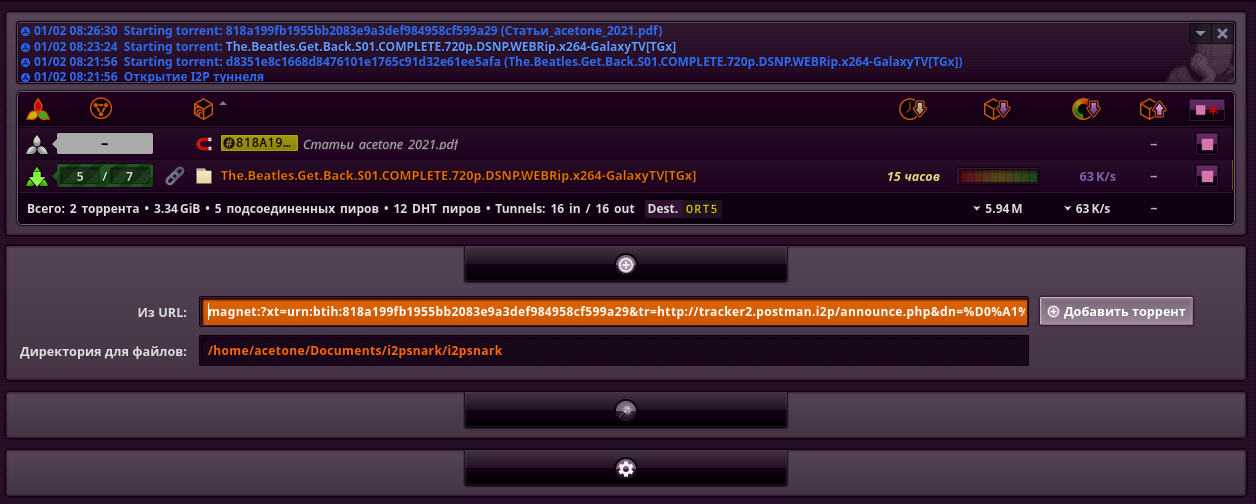
In the "From URL" field you can insert a magnet link or a direct path to the file .torrent on your file system. The "Data dir" field specifies the path where the downloaded files will be saved. To start the download, click "Add torrent"".
I2PSnark also supports maggot links, a type of magnet introduced in the Robert I2P torrent client. Now Robert and his quirks are out of use. Today the term "maggot link" is found mainly as a misnomer for standard magnets..
The second and, in some cases, more elegant option allows you to add a torrent without using the web interface: add the torrent file of the desired distribution to the main I2PSnark file storage directory. By default, I2PSnark stores torrent files and downloads in a subdirectory of the same name i2psnark/i2psnark. When you add a new torrent file to this directory, the application will pick it up and begin the download process automatically within a few seconds.
To create a new torrent, you need to use the button with the magic wand icon. All that is required of us is to indicate the full path to the distributed file or folder in our file system and select trackers that will be immediately added to the distribution. If you create a distribution without using trackers, the search for peers will be exclusively based on DHT. If you are not sure what to do, check the box next to each proposed tracker and select one as the main one. As a rule, Postman is the main one, since it is the oldest classic torrent tracker with a forum (http://tracker2.postman.i2p).
After clicking the "Create torrent" button, a distribution will be created and will appear in the general list. For convenience, it is recommended to add distributed files to the default I2PSnark folder so that everything is in one place.
The finished torrent file will appear next to the other torrent files, from where you can take it for posting on the forum or directly transferring it to someone. If you click on the name of the distribution in the I2PSnark web interface, a window with information will open. 
In the upper right corner you can find infohash distributions, a magnet link (icon with a magnet) and a link to download a torrent file (rightmost). When you click on the torrent file icon, you will be offered to download the file, which is located in the already designated location. To send a magnet link, right-click on the corresponding icon and copy the link to which it leads. This is a magnet link, ready for publication..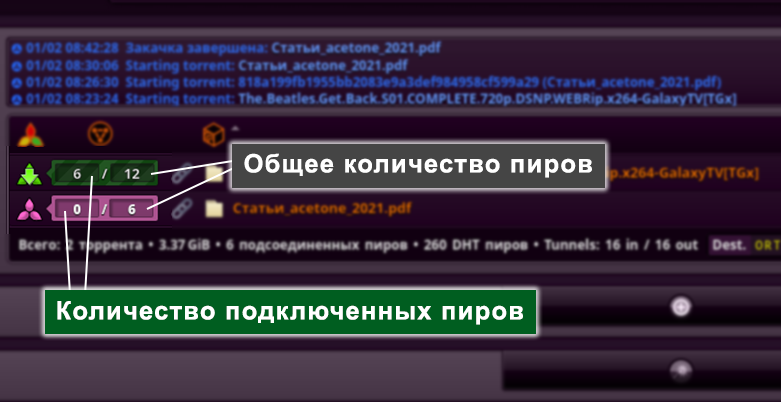
Having created a distribution that you really consider important, try to ensure the maximum seeding time so that at least the first few peers can download the entire files. After downloading someone else's distribution, do not leave immediately, sit for a while if time and disk space permit. Gentlemanship is appropriate everywhere.
Getting to know I2P torrent trackers is beyond the scope of this article and falls entirely on your shoulders. However, there is nothing complicated: design the distributions clearly, informatively and beautifully.
Seedbox
Seedbox is a device used for constant distribution of files. As a rule, it is assembled from single-board computers and external HDDs. However, any device that can simultaneously run an I2P router and a torrent client with the maximum possible uptime and disk space will do. Seedboxing includes not only the constant distribution of your files, but also support of other people’s distributions at least during the release week. This is a kind of subculture focused on the free exchange of information, imbued with altruism and price tags on hard drives.
Someday we, enthusiasts, will get to a detailed review of a successful assembly of a seedbox from sticks and electrical tape, but for now we will limit ourselves to advice:
The minimum amount of device RAM to run i2pd and I2PSnark is 512MB, with a comfortable margin of 1GB.
In the future, active distribution of torrents has a bad effect on the lifespan of hard drives, since torrenting involves active work with the disk with constant changes in reading locations. Especially if there is a simultaneous distribution to many participants. Because of this, multiple smaller disks should be preferred over, for example, one multi-terabyte disk. This will increase the overall system performance, and the failure of one disk will not lead to complete loss of information. Unless of course you get to use RAID — systems for mirroring drives among themselves to prevent loss of information if one of them breaks down.
Due to the likelihood of disk failure, it is advisable that the operating system be on a separate physical disk than where the torrent content is stored. This is especially acute for single-board computers, where the operating system runs on an SD drive, which itself is not known for its durability..
The topic of seedboxes based on budget single-board devices is becoming especially relevant in light of the news about the release of the Linux kernel 5.15 with support for SMB and NTFS, which opens up new horizons for weak hardware, but this is a topic for another discussion...
P.S
Decentralization and the development of free technologies are impossible without the participation of ordinary people. If we do not want to depend on the policies of file hosting services and restrictions on the part of the provider, everyone needs to make a contribution within their power. At the initial stage of popularization of I2P torrents, seedboxing is a critical element that contributes to the development of the technology. Already today, torrents on hidden networks are common in countries where the situation forces it. Gradually, the practice of bans and fines is spreading to other regions. Think about it: is it possible for you to allocate several thousand rubles to buy a single-board computer and a pair of hard drives to organize your own seedbox? Even if you have not dealt with Linux and do not understand what connecting via SSH is, believe me, entering the exciting game of free technologies and openness will pay off all the hours and nerves spent on mastering these basics. In my opinion, the culture of free software and hidden networks allows each user to be an equal participant, a keeper of technology and information, which is no worse than a top online game, but with one big difference: you are not degrading, but developing.

